Security Threat Analysis
Security threats are analyzed in the lifecyle of consumer-presented codes, which includes the following stages:
- Code generation and storage
- Transaction processing
- Message transmission
In addition to the threats, general guidelines are also provides in each stage to protect business security.
Overview
You can see security threats in the figure below:
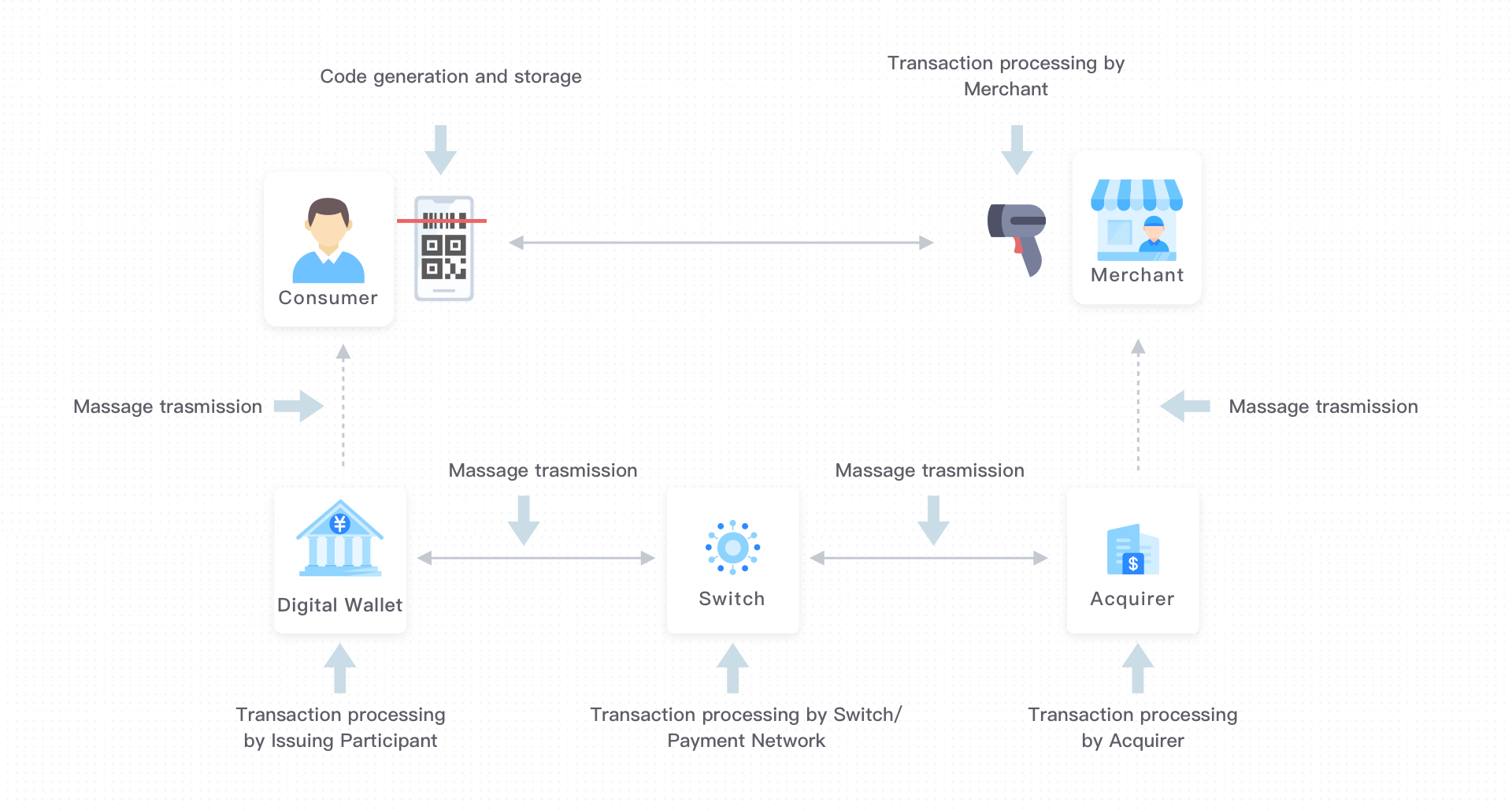
Figure 4. Threats of consumer-presented mode
For each threat, a guideline is introduced for you to mitigate the threat.
Code generation and storage
Threat:
Code values are disclosed in screenshots when users display the code on mobile devices.
Guideline:
The time period when users display the code value shall be limited. After the time period, the code value shall become invalid.
Users should be prohibited from capturing screens in the app. For example, the app presents a warning message or a screen protection page to prevent users from capturing screens.
Threat:
The code value generation and verification process might be exposed to brute force attacks.
Guideline:
To prevent brute force attacks, user account information, device information, and merchant information should be checked in the code value generation and verification process.
Digital Wallet should have the capability to detect robot automatic attacks, such as credential-stuffing attack that obtains user password.
General Guideline:
Digital Wallet should ensure that the barcode generated for a consumer is associated with the consumer's payment account.
Digital Wallet should obtain consumer authorization before enabling code-scanning payment services. In addition, PSP should provide the consumer with the option to turn off code-scanning payment services.
The generated barcode should not contain sensitive information of the customer and the payment account, including but not limited to consumer's mobile phone number and birthday.
Transaction processing
For merchant
Threat:
Merchants cannot correctly process the code value after scanning the code, because of the following:
- Bar code format is not supported.
- Code value is compromised.
Guideline:
Merchants should use bar code acceptance devices that meet the requirements of local regulators.
Threat:
Merchant cashier system is vulnerable to attackers who might steal the code values and use them in other payments.
Guideline:
Merchants should use bar code acceptance devices that meet the requirements of local regulators.
For acquirer
Threat:
Acquirers cannot correctly process and route the transaction, which may result in transaction failure or user funds losses, because of the following:
- Bar code value is not supported.
- Code routing rules are conflicting.
Guideline:
Follow the instruction as described in Transaction Processing.
For Switch
Threat:
Merchant cashier system is vulnerable to security risks, such as physical security, host security, network security, and application security.
Guideline:
Risk management system should be in place for code-scanning payment to monitor, identify, and prevent risk transactions. Information such as environment data (IP, location, and so on), user habits, seller account characteristics, and user equipment data can be used to enhance the risk management system.
For digital wallet
Threat:
The user authentication mechanism is not strong enough.
Guideline:
Digital Wallet system should have effective technical means to effectively verify the user identity.
Threat:
The risk management system is not effective enough to identify and prevent risk transactions.
Guideline:
Risk management system should be in place for code-scanning payment to monitor, identify, and prevent risk transactions. Information such as environment data (IP, location, and so on), user habits, seller account characteristics, and user equipment data can be used to enhance the risk management system.
General Guideline:
Dynamic barcode should be used to prevent a code from being reused which may cause duplicate deductions, and the dynamic bar code should be effective within a specific time period after being generated and can be automatically updated within a specific time frame.
Message transmission
Threat:
Man-in-the-middle attack: Attacker may modify transaction messages for attacking purposes.
Guideline:
To ensure the confidentiality and integrity of the transmitted data, security methods such as digital signature and encryption should be adopted to protect the sensitive information enclosed in the transaction message.
Conduct secure and reliable data interaction by using security protocols and strong encryption algorithms to secure transaction communication links. Update security protocols to the latest stable versions timely.
Threat:
Replay attack: Attacker may replay a transaction request multiple times by using a previous successful transaction message.
Guideline:
The time period when users display the code value shall be limited. After the time period, the code value shall become invalid.
The transaction message should contain dynamic parameters such as random number, time stamp, or one-time session token, to prevent replay attacks.
Conduct secure and reliable data interaction by using security protocols and strong encryption algorithms to secure transaction communication links. Update security protocols to the latest stable versions timely.
General Guideline:
The code-scanning payment transaction messages should be configured with correct transaction type to identify the real business scenario. The integrity, authenticity and traceability of the transaction information should also be ensured.
After the payment transaction is completed, both the merchant acceptance terminal and the user mobile terminal should display the payment result. In addition, if the payment fails, the reason for the failure should also be displayed.
More information
In addition to these security guidelines, you also need to comply with other guidelines, requirements and recommendations. For more information, see General Guidelines, Requirements and Recommendations.
